How to Lower Azure Bandwidth Cost Effectively (Xray+WARP)
A guide on reducing Azure bandwidth expenses using Cloudflare services, Xray-core, and WireGuard for efficient traffic management.
Managing cloud costs is crucial for businesses that leverage Azure Virtual Machines (VMs) to host VPS servers. Below, we outline a practical strategy for significantly reducing Azure bandwidth expenses using Cloudflare's services and efficient traffic management techniques.
Utilize Cloudflare’s Bandwidth Alliance
Cloudflare partners with Azure under the Bandwidth Alliance, which provides cost savings on data transfer fees. By routing all traffic through Cloudflare’s Content Delivery Network (CDN) or WARP service, you can cut your bandwidth costs by up to one-third.
Leverage Xray-core and WireGuard
To maximize the benefits of WARP’s free configurations, we can use Xray-core with the WireGuard interface. This setup ensures seamless connectivity while leveraging WARP’s capabilities for free bandwidth.
Overcome WARP’s Speed Limitations
Each WARP interface has a speed limit of 400 Mbps. To achieve higher throughput, implement load balancing across multiple WARP interfaces using Xray-core. Assume we have a VPS with a 1 Gbps dedicated port. So we set three WARP interfaces and load balance between them:
Configuration:
-
Set up three WARP interfaces with WireGuard kernel:
-
Install WireGuard:
- If Ubuntu = 24.04 LTS:
sudo apt install wireguard -yq - If Ubuntu < 24:
sudo apt install resolvconf wireguard-dkms wireguard-tools -yq
- If Ubuntu = 24.04 LTS:
-
Generate three WARP configs:
- Download and set up the
wgcfprogram corresponding to your server architecture. For example, for amd64:wget https://github.com/ViRb3/wgcf/releases/download/v2.2.24/wgcf_2.2.24_linux_amd64 mv wgcf_2.2.24_linux_amd64 /usr/bin/wgcf chmod +x /usr/bin/wgcf - Register and generate WARP config profile:
wgcf register wgcf generate - Add the
Table = offline to the generated WireGuardwgcf-profile.conffile (below MTU).
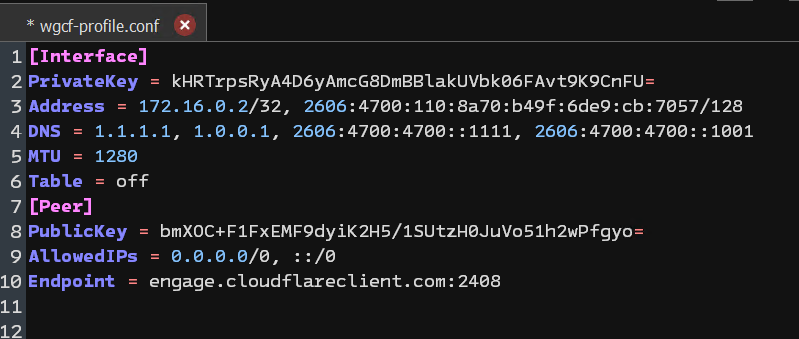
- Download and set up the
-
Configure WireGuard and enable the first interface:
sudo mv wgcf-profile.conf /etc/wireguard/warp1.conf sudo systemctl enable --now wg-quick@warp1Note that we renamed the
wgcf-profile.conftowarp1.conf. This is our first WARP interface. Repeat this process to generatewarp2.confandwarp3.conf. Ensure all configuration files are in the/etc/wireguard/directory. For generating new WARP profiles, delete thewgcf-account.tomlfile and re-run thewgcf registerandwgcf generatecommands.
-
-
Configure Xray-core:
-
Configure Xray
outbound: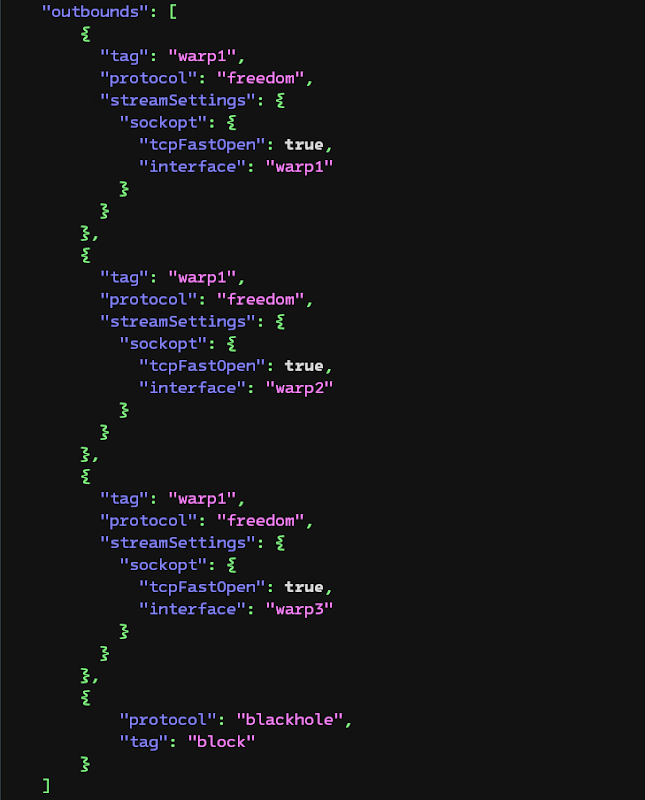
-
Configure Xray Routing:
- Add a
balancerrule in theroutingobject: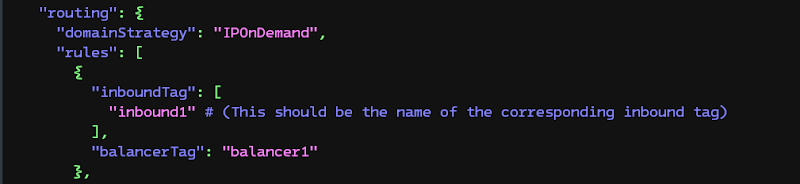
- Create the
balancersobject: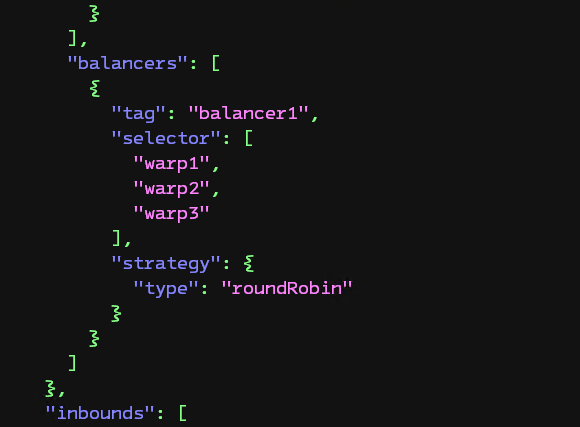
- Add a
-
Notes:
- When using
LoadBalancingin Xray-core, ensure that thedomainStrategyin theroutingobject is set toIPOnDemand. - If your inbound configuration does not have a tag, add one. This tag will be referenced in the
inboundTagwhen defining thebalancerrule.
Benefits and Additional Features
This approach leverages load balancing across multiple WARP interfaces to distribute traffic evenly, effectively increasing total bandwidth capacity and optimizing port utilization. However, using more than six WARP interfaces with load balancing can lead to significantly increased resource usage in Xray-core, potentially impacting system performance. For this reason, it is recommended to limit the number of WARP interfaces to four (the lower, the better), which strikes a good balance between performance and resource efficiency.
In addition to improving traffic management, this method offers substantial cost savings. By distributing bandwidth usage across WARP interfaces, Azure bandwidth costs can be reduced from approximately $0.08 per GB to around $0.03 per GB. This makes it a cost-effective solution for managing high-bandwidth requirements while maintaining system stability.
In emergencies, "porn" traffic can be blocked either through “geosite” files or DNS blocking (e.g., Cloudflare Family) to further reduce bandwidth usage by approximately 20%. This figure is based on extensive experimentation over several months on Iranian networks.
This solution, powered by CompassVPN, offers a streamlined and automated approach to VPN setup and management, running seamlessly on a VPS. With a one-command setup, it enables remote monitoring, central dashboard integration, and automatic collection of VM metrics like CPU, memory, and traffic. It automates Cloudflare DNS and TLS certificate management, supports direct or proxied configurations, and optimizes connections with WARP auto-rotation. Additional features include automatic updates, configuration rotation, and blocking of torrents, ads, malware, phishing, and Iranian websites. Integration with Grafana Cloud or Pushgateway ensures efficient metric visualization, while Xray-Knife verifies configuration reliability. Custom DNS options further enhance performance and cost efficiency, making CompassVPN a professional and comprehensive solution.
─ Source: Google